I am gonna write some cool Computer tricks that I think the majority of peoples don't know about. Well, some people already know about these tricks thus if you are one of them so comment below and let us know and also tell us about many other useful tricks, So here we go...
1. The Hidden folder :
Well, technically it's just a folder hidden in plain sight. You can use it to store your data which you don't want to share with your Family, Boss or with your Partner or you can also use it to store your 100GB study material😉.
Let's know how we can create a hidden folder...
-> First of all, create a new folder or choose an existing one which you want to hide.
-> After that, you have to Rename your folder by pressing F2 or Right-click on the folder and choose Rename option.
-> While Renaming it hold the "Alt" key and press "0160" form your Numberpad.
-> Now you got a folder without any name as like below.
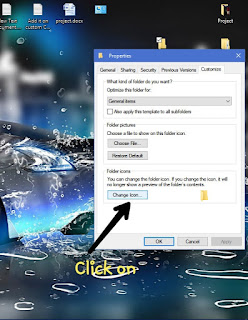
-> Now again Right-click on the folder and then go to Properties and then click on Customize and then click on Change icon as given below...
Boom...now you have a secret folder for yourself.
If you want to Hide a File or Folder thus anyone can never access those without your permission then check out the below link...
How to hide a file or folder permanently...
-> While Renaming it hold the "Alt" key and press "0160" form your Numberpad.
-> Now you got a folder without any name as like below.
-> Now again Right-click on the folder and then go to Properties and then click on Customize and then click on Change icon as given below...
Boom...now you have a secret folder for yourself.
If you want to Hide a File or Folder thus anyone can never access those without your permission then check out the below link...
How to hide a file or folder permanently...
2. The Super Kill :
Well, we all have a pc which gets hanged sometime and then we open Task manager to kill tasks but sometimes our pc get hanged to the extent that we can't even use Task manager or it's shows blank, then you can use this Method ( Only works in Windows 10). What we going to do here is the use of Windows 10 multiple virtual desktop feature...
-> First of all, you have to create a virtual desktop by pressing "Ctrl+Window+D".
-> You get now you have another virtual desktop as shown below.
-> Thus when you PC gets Hanged then press "Ctrl+Window+D" together then you get moved at your second virtual desktop.
Also, Read - Best Ethical hacking Forums.
-> Thus when you PC gets Hanged then press "Ctrl+Window+D" together then you get moved at your second virtual desktop.
Also, Read - Best Ethical hacking Forums.
-> Well, now you have to open Task manager here by pressing "Ctrl+Shift+Esc" together ( Make sure you didn't open your task manager at your first Virtual desktop ) then you will get your task manager opened here without any trouble and you can end or manage every task which is running on all of your desktops...or just end your task which is the reason for Hanging your PC.
3. The Pro Snipper :
This new snipping tool is seriously underrated. Every time when you suffering on the internet or doing something on your pc and quickly want to cut a part of your screen which can be useful for you then you can use this tool to quickly snip a portion of your screen and modify them in the improved snipping tool.
-> All you have to do is press "Shift+Window+S" key combination together and drag your mouse pointer on that portion which you want to snip as given like below...
-> Now you have to open any application where you want to modify it, Like as I am gonna open MS Paint.
Also, Read - What's a computer virus?
-> Now you have to press "Ctrl+V" here for paste your snipped part.
As you can see it's much easier than first take a screenshot and after that crop to getting your best part. It's work like as just cut and paste, isn't cool!
4. Godmode Folder :
Basically, this folder is used to access all of your 206 computer features on a single easy-to-scroll-through interface. To make this work you must be using an account with administrative privileges.
-> First of all, you have to create a New folder on your desktop.
-> Now you have to rename the folder by the following string or name.
"GodMode.{ED7BA470-8E54-465E-825C-99712043E01C}"
-> After renaming by the above name properly, you'll notice that the folder icon changed to a control panel icon.
Also, Read - How to Hide a Hard drive partition?
-> Now you have to open the newly created Godmode Folder, thus you will get an interface like as given below.
5. The Quick Shot :
This is just a simple trick to open task buttons or Quick launch program quickly.
-> Each program has an assigned number as given below...
-> You can open any application which is pinned at your taskbar by pressing "Window+Assigned no.".
So guys, if you are getting any problem in the above tricks then you can comment below and don't forget to share with others and let them know...